Bybit Hack Uncovered – The Largest Digital Heist
On February 21, 2025, the crypto community was stunned by what is being called the biggest digital heist ever. Hackers exploited a vulnerability during a routine transfer of Ethereum from an offline “cold” wallet to a “warm” wallet, resulting in losses exceeding $1.5 billion. In a dramatic response, Bybit’s CEO reassured users that despite the breach, every client’s assets remain 1-to-1 backed, pledging full reimbursement to those affected—even if the stolen funds cannot be recovered.
This unprecedented event not only shook market confidence (with Ethereum’s price dipping by nearly 4% in the immediate aftermath) but also ignited a global conversation on the evolving threats in crypto security.

Inside the Attack – A Deep Dive into the Breach
Founded in 2018 and backed by notable figures such as former Paypal chief Peter Thiel and even reportedly having early support from US President Donald Trump, Bybit has grown rapidly and now serves more than 60 million users worldwide.
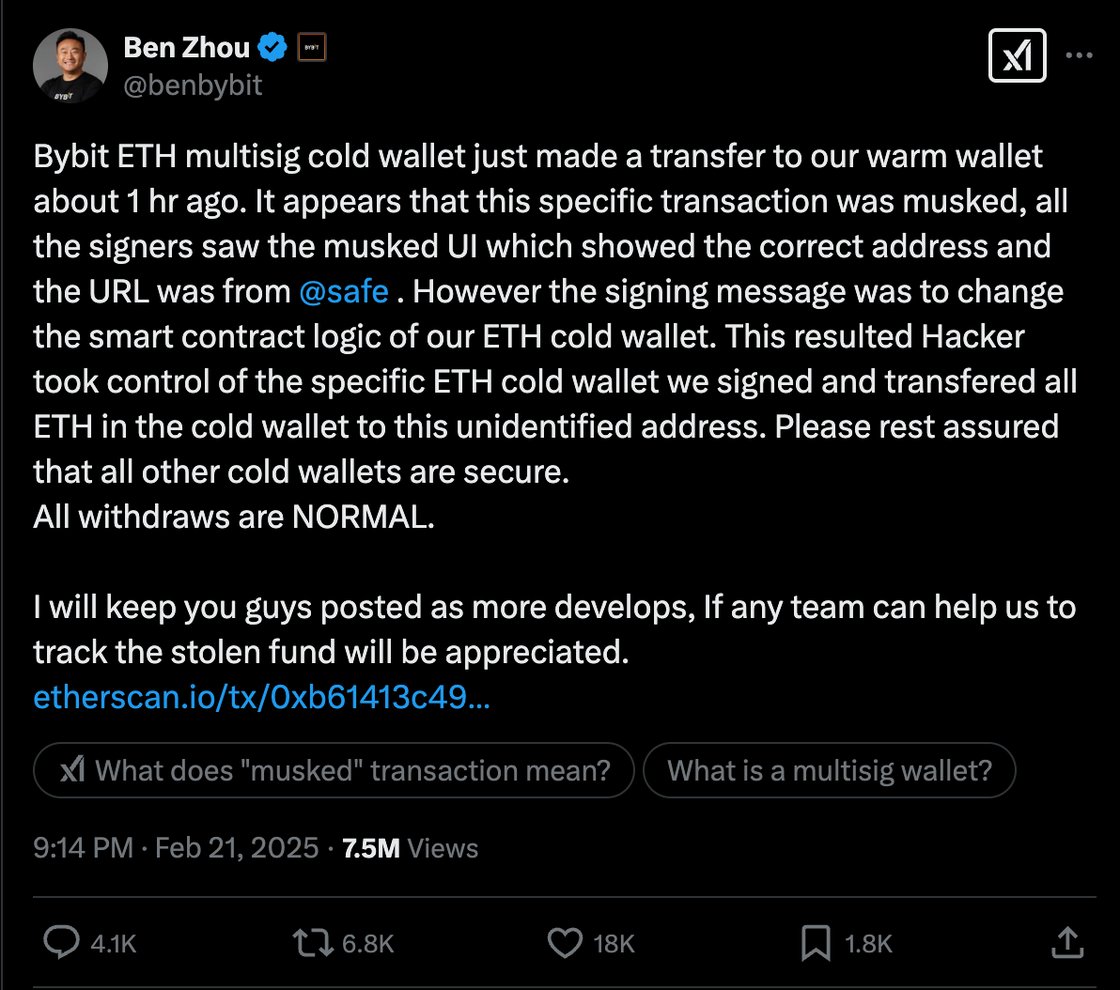
Forensic investigations show that the Bybit hack was not a simple mistake—it was a carefully planned attack. Here’s what happened, explained in simple terms:
When Bybit was making a routine transfer of Ethereum from a secure “cold” wallet to a “warm” wallet used for daily trading, the attackers stepped in. They used advanced methods to hide important details of the transaction. This meant that while everything looked normal on the surface, the hackers were secretly changing the rules that control how the funds are moved.
Normally, Bybit’s multi-signature (multi-sig) system requires several approvals for a transaction, which should catch any errors or unusual activity. However, the attackers found a weakness in this system. By manipulating the signing process, they altered the smart contract logic—the set of rules that governs the transaction—without triggering any alarms. In other words, they slipped past the usual security checks.
Shortly after the breach, over 350,000 withdrawal requests flooded the platform as anxious customers rushed to secure their funds. This surge in requests not only overwhelmed the system but also underscored the wide-reaching impact of the attack on user trust and operational capacity.
In response to the crisis, Bybit reached out to “the brightest minds in cybersecurity and crypto analytics” by launching a recovery bounty program. The company offered a reward of 10% of any recovered funds, which could have totaled up to $140 million, to encourage ethical hackers and security experts to help track down and recover the stolen assets.
The Bybit breach is a stark reminder that even major players in the crypto space could be vulnerable to sophisticated attacks. It highlights the urgent need for stronger security measures and more transparent transaction processes.
Rethinking Security Protocols – Lessons and Best Practices

The Bybit hack serves as a crucial reminder of the vulnerabilities inherent in current crypto security infrastructures.
Enhance Transaction Transparency & Eliminate Blind Signing
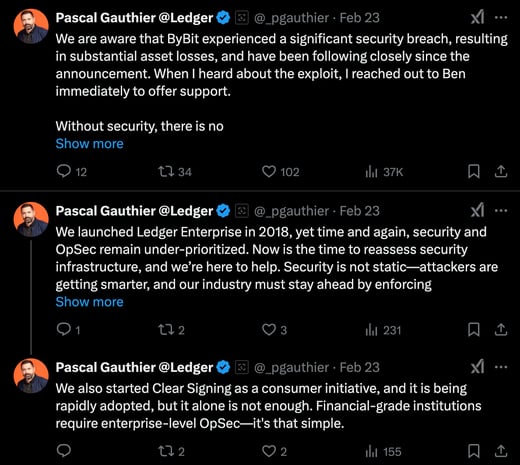
One of the major risks in crypto security is blind signing—approving transactions without a clear view of the underlying details. As Pascal Gauthier, CEO of Ledger, notes, even with the launch of Ledger Enterprise in 2018, security and operational practices often fall short of what is needed. Gauthier emphasizes that “Clear Signing” is vital. This method ensures that every transaction is fully visible before approval, making it far more difficult for attackers to manipulate transaction data without detection.
Transition from Traditional Multi-Signature to Distributed MPC Wallets
While multi-sig wallets have been the industry standard, their vulnerabilities are becoming more apparent. Distributed Multi-Party Computation (MPC) wallets address this by splitting key control among several parties. This distributed approach minimizes the risk associated with a single point of failure and provides a much stronger defense against sophisticated attacks.
Strengthen Enterprise Governance and Approval Processes
Robust internal controls are crucial for mitigating security risks. Organizations should implement multi-layered approval processes—such as requiring sign-offs from multiple executives for large transactions, whitelisting trusted wallet addresses, and utilizing hardware-based verification methods. Integrated financial management solutions like Request Finance can play a pivotal role here. By automating compliance and risk assessments, Request Finance helps streamline governance, ensuring your organization remains audit-ready and resilient against potential threats.

Adopt Off-Exchange Trading Models to Secure Assets
Relying solely on exchange-controlled wallets increases exposure to potential breaches. Off-exchange trading solutions, such as Ledger’s Tradelink, enable institutions to trade while keeping funds in segregated collateral accounts. This approach not only secures assets more effectively but also mitigates counterparty risk, ensuring liquidity without exposing assets to unnecessary vulnerabilities.
Implement a Proactive Breach Response Strategy
When a breach occurs, swift and decisive action is critical. Pausing withdrawals, launching thorough investigations, and reinforcing internal safeguards are essential steps to minimize damage. The prompt crisis management demonstrated by Bybit’s leadership underscores the importance of having a well-prepared response strategy.
Bybit has acted swiftly since the breach. The platform has successfully closed the ETH gap, and a new, fully audited Proof-of-Reserves (POR) report will be published soon. This upcoming report will verify that Bybit has once again restored full 1:1 backing for client assets using a Merkle tree structure. This decisive action reaffirms their commitment to transparency and security—a critical benchmark for the crypto industry.
As we continue to learn from these events, it’s clear that robust security measures and proactive governance are essential for protecting user assets and maintaining trust.


